API authentication is the process of verifying the identity of a user or a system that is making a request to an API. It is used to ensure that only authorized users or systems are able to access the API and its resources.
Authentication is a way to verify a user before the log into an application, and authorization defines what the user can access.
Basic Authentication
This is the simplest form of authentication, where a user provides a username and password in the request header, and the API checks the credentials against a database of users.
It uses username and password encoded in a variant of Base64.
The username and password can be passed in a header request as follows:
Authorization: Basic amFnZGVlcDp0ZXN0MTIz
Session Based Authentication
For accessing resources on the server over HTTP, the client reserves a session with an identification on the server and further communication is established using the same identification.
The server sends a SESSIONID in the header response to the client and further communication is established based on the SESSIONID on the server.
Sessions are short lived, and we can set the expiration time in the header.
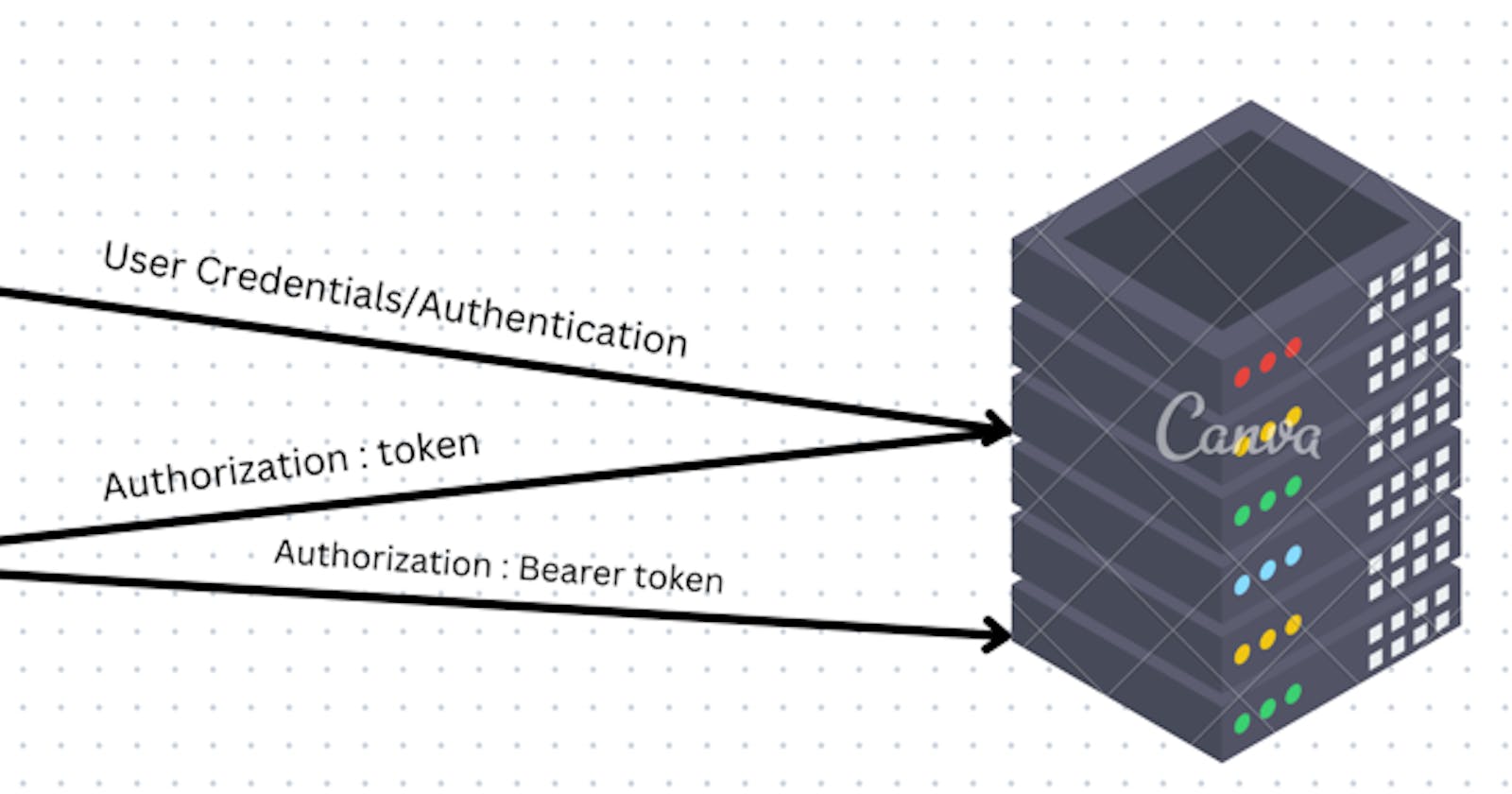
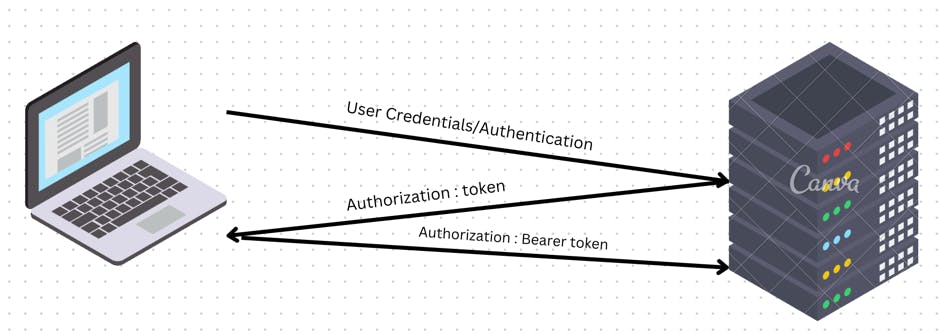
Token-Based Authentication
This type of authentication uses a token, which is a unique string that is generated by the server and sent to the client. The client then sends the token back to the server in subsequent requests, and the server uses the token to verify the identity of the client.
A user logs into the application using the credentials and gets a token to access the application. The token is valid for a certain period of time
A token supports a stateless connection over HTTP where the server sends the token to the client as a header response. After that, each time the client requests a resource, the token needs to be sent in the header.
The server sends the token in the response header on the /auth (authenticating a user) call.
Authorization: eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImV4cCI6MTYzODgxNDQxNSwiaWF0IjoxNjM4ODEyNjE1fQ.UVAmFYlDn0X5GhF987Wz8p0bABDoHWI7KujPCb99x-8
- The client sends the bearer token in the request header, as shown:
Authorization: Bearer eyJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJhZG1pbiIsImV4cCI6MTYzODgxNDQxNSwiaWF0IjoxNjM4ODEyNjE1fQ.UVAmFYlDn0X5GhF987Wz8p0bABDoHWI7KujPCb99x-8
This says that the bearer of the token should be given access to the server resources. The server does not need to remember the session or the state. Instead, this is taken care of by the client via the token. This helps in improving the performance of the server.
OAuth2
OAuth2 is an open standard for authorization that provides a secure way for users to grant access to their resources on one site, to another site, without sharing their credentials. It is commonly used as a way for users to log in to third-party applications using their Google, Facebook, or Twitter accounts, among others. This allows users to grant limited access to their accounts without giving third-party applications full access to their personal information. OAuth2 is widely used by many different websites and applications, and is often used as a way to provide secure access to APIs.
OAuth 2.0 supports different types of grants, which determine how the client obtains the token. Common grant types are:
Authorization Code: The client redirects the user to the authorization server, which then redirects the user back to the client with an authorization code. The client can then exchange the code for an access token.
Implicit: The client redirects the user to the authorization server, which then redirects the user back to the client with an access token.
Password: The client directly requests an access token by providing the user's credentials.
Client Credentials: The client requests an access token by providing its own credentials.
OpenID Connect
This is an extension of OAuth 2.0 that provides an additional layer of security by adding an identity layer. It allows the client to verify the identity of the end-user based on the authentication performed by an authorization server, as well as to obtain basic profile information about the end-user in an interoperable and REST-like manner.
Reference - Learn API Testing: Norms, Practices, and Guidelines for Building Effective Test Automation (Book)